Originally published on May 29, 2025, to announce the general availability of SonarQube Advanced Security for SonarQube Server, this blog post has been updated to reflect the general availability of Advanced Security for SonarQube Cloud.
Sonar is thrilled to announce a major leap forward: the General Availability (GA) of SonarQube Advanced Security! Building on the foundation trusted by over 7 million developers and 400,000 organizations for industry-leading code quality analysis, SonarQube now delivers the first fully integrated solution for developers to find and fix both code quality and code security issues across their entire codebase. This includes first-party code, AI-generated code, and the third-party open source dependencies that form the backbone of modern applications. This unified approach moves beyond fragmented tooling, bringing comprehensive security and quality analysis directly into the developer workflow—where it belongs.
Why comprehensive code security matters now more than ever
Software development today is a high-velocity race. Teams are building faster than ever, often leveraging the power of AI-generated code and assembling applications with the help of a vast ecosystem of third-party open source libraries. Reports show that 70-90% of modern applications consist of open source code, and the reliance on AI is skyrocketing, with over 62% of developers now making use of AI coding tools. While both AI and open source can supercharge innovation, they also dramatically expand the potential attack surface. Supply chain attacks are on the rise, and traditional security tools often struggle to keep pace, frequently overwhelming developers with noise, creating friction in workflows, and catching issues too late in the cycle.
The expanded reliance on external code, whether from open source repositories or AI generation tools, introduces new security complexities. Third-party libraries can harbor known vulnerabilities (such as CVEs) or carry restrictive licenses that create legal risks. AI-generated code, while powerful, can sometimes introduce elusive flaws, quality issues, or insecure patterns that are difficult to spot.
Trying to manage these accelerating risks with a collection of separate solutions for Static Application Security Testing (SAST), Software Composition Analysis (SCA), secrets detection, and Infrastructure as Code (IaC) scanning often leads to inefficiencies - specifically when operated by different teams. Developers are overwhelmed by context switching, alert fatigue from excessive false positives, inconsistent results across tools, and difficulty correlating findings to understand the true risk picture. When developers are overwhelmed by security inputs, the security output – better bottom line security – will suffer. Why?
Security tools are only effective if developers actually use them.
Tools that disrupt workflows, generate overwhelming noise, or require complex configuration often get sidelined, leaving vulnerabilities undetected until it's much more costly and difficult to fix them. Sonar's developer-first philosophy directly tackles this problem. By integrating comprehensive security capabilities seamlessly into the tools developers already use, SonarQube Advanced Security makes security a natural part of the development process, not a bolted on afterthought.
Integrated code quality and code security
While SonarQube is widely recognized for its industry-leading code quality analysis capabilities, its core security capabilities have steadily expanded over the years. Now, SonarQube is the industry leader for integrated code quality and code security in one package.
The core security features already available in SonarQube empower developers to secure their first-party and AI-generated code:
- SAST: SonarQube's powerful SAST engine analyzes your source code to detect a wide range of security vulnerabilities and weaknesses before they reach production. It identifies issues like weak cryptography, insecure communication or authentication, buffer overflows, and more across the most popular programming languages and frameworks. Think of it as an intelligent scanner for the code you write directly.
- Taint analysis: This advanced data flow analysis technique tracks potentially untrusted user input as it moves through your application, even across multiple files and functions. It's crucial for uncovering complex injection vulnerabilities like SQL injection and cross-site scripting (XSS), by ensuring data from external sources is properly validated or "sanitized" before interacting with sensitive parts of your system, like databases or the operating system.
- Secrets detection: This feature acts like a security guard for your codebase, automatically scanning for accidentally hard-coded sensitive information like API keys, passwords, database credentials, and security tokens. Leaked secrets are a common vector for breaches. SonarQube uses hundreds of patterns (and supports custom patterns in Enterprise Edition) to detect secrets, preventing them from ever being committed to your repository, especially when used with SonarQube IDE extension.
- Infrastructure as Code (IaC) scanning: Cloud infrastructure is often defined in code using tools like Terraform, CloudFormation, Kubernetes manifests, Azure Resource Manager, and Ansible. IaC scanning analyzes these configuration files to detect misconfigurations and security risks before your infrastructure is deployed, helping ensure your environments are secure from the ground up.
These core security capabilities provide essential protection for human-written and AI-generated code. They uncover hidden injection flaws, stop exposed secrets, and secure cloud environments by finding infrastructure code misconfigurations, significantly reducing breach risks and costly rework to protect your reputation and bottom line. Now, SonarQube Advanced Security extends this protection to include open source code and the rest of the software supply chain.
SonarQube Advanced Security: developer-first security for all code
SonarQube Advanced Security, available for SonarQube Enterprise (and higher), represents a significant leap forward, extending SonarQube's powerful analysis capabilities to protect your entire software supply chain, with a particular focus on open source dependencies. This is achieved through two major capabilities: SCA and advanced SAST.
Software Composition Analysis (SCA)
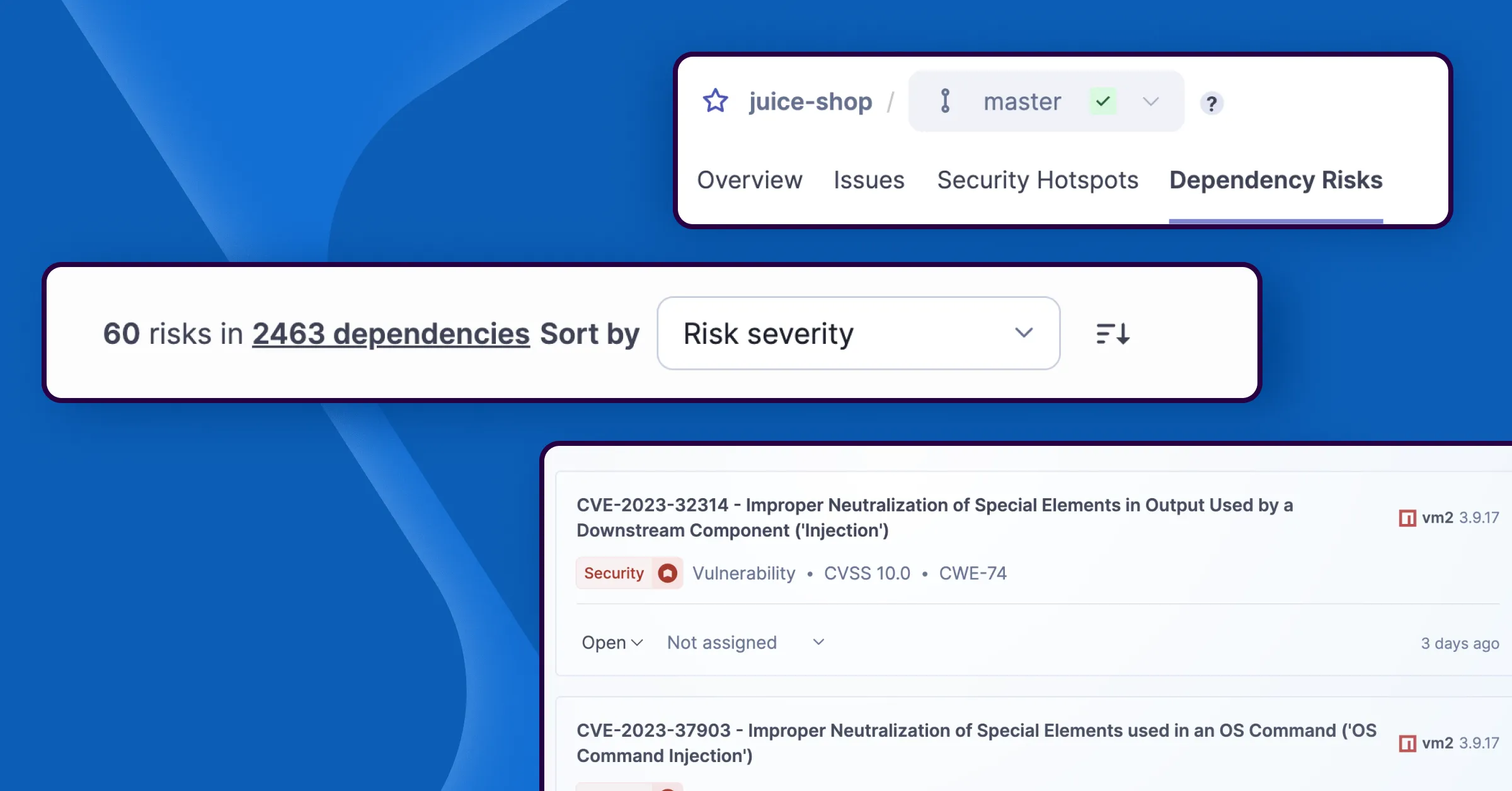
SCA is the process of identifying and analyzing the components used within your applications. Given that open source constitutes the vast majority of modern codebases, understanding the risks associated with these components is critical. SonarQube's SCA capabilities provide comprehensive visibility and control:
- Vulnerability detection: Automatically identifies known vulnerabilities (CVEs) listed in public databases (like NVD) within both your direct dependencies (libraries you explicitly include) and transitive dependencies (libraries your dependencies rely on). For each vulnerability found, SonarQube provides crucial context, including its severity (CVSS score), EPSS (Exploit Prediction Scoring System), the affected component versions, information on available patches or fixes, and remediation guidance, enabling proactive defense against known exploits.
- License compliance: Open source components come with licenses that dictate how they can be used. Violating these licenses can lead to significant legal and compliance issues. SonarQube automatically identifies the licenses of all dependencies and helps ensure they comply with your organization's policies, flagging potentially incompatible or problematic licenses. This simplifies the complex task of managing open source license risk.
- SBOM Generation: Automatically generates a Software Bill of Materials (SBOM) in standard formats like CycloneDX and SPDX. An SBOM is a detailed inventory of all software components and dependencies in your application. This provides essential transparency for security audits, compliance requirements (like those documented in the NIST Secure Software Development Framework (SSDF), mandated by US White House Executive Order 14028, and other related government actions), and rapid response if a new vulnerability is discovered in a component you use.
SonarQube's SCA fucntionality currently supports popular ecosystems including Java, Kotlin, Scala (Maven, Central), JavaScript and TypeScript (npm), Python (PyPl), C#/.NET (NuGet), Go, PHP, Rust, and Ruby, with a commitment to expanding language coverage in future releases.
Advanced SAST
While SCA focuses on known vulnerabilities in dependencies, SonarQube’s advanced SAST tackles a different, often overlooked problem: vulnerabilities that arise from the interaction between your code and the code within third-party libraries.
Traditional SAST tools often treat libraries as "black boxes," analyzing your code but not tracing data flow into or out of the library code itself. This can miss critical vulnerabilities where, for example, tainted user input is passed to a library function that uses it unsafely, or where a library returns unsafe data that your application then misuses.
SonarQube's advanced SAST overcomes this limitation. It extends SonarQube's powerful taint analysis engine to trace data flows in and out of the code of third-party libraries. By analyzing how your application actually uses these dependencies, advanced SAST can uncover deeply hidden, complex vulnerabilities that traditional SAST tools simply cannot find. It provides a much deeper and more accurate understanding of the security risks associated with using open source components.
Improving supply chain security proactively with the help of open source maintainers
SonarQube Advanced Security is also the first step in integrating the unique capabilities Sonar acquired with Tidelift. Sonar takes a proactive approach to improving open source security by paying the maintainers of open source projects to follow secure software development practices - and document the practices they follow.
While standard SCA relies heavily on public vulnerability databases, this collaboration also provides verified, curated intelligence that goes beyond basic CVE information. Exclusively within SonarQube, you benefit from these maintainer insights on:
- False positive verification: Confirmation on whether a reported CVE actually affects a specific package version or usage context.
- Exploitability context: Information on whether a vulnerability is practically exploitable in real-world scenarios.
- Workarounds and recommendations: Guidance on mitigating risks when a direct fix isn't immediately available.
This layer of human-curated intelligence promises to significantly reduce the noise often associated with dependency scanning, allowing development and security teams to focus their efforts on the risks that truly matter, saving valuable time and accelerating remediation.
Additional new security capabilities in SonarQube Server and Cloud
SonarQube Server 2025.3 release and SonarQube Cloud bring other valuable enhancements reinforcing our commitment to continuous improvement:
- Expanded secrets detection: The secrets detection engine now covers significantly more ground, featuring an expanded library of over 400 secret patterns and continued support for custom patterns (in Enterprise Edition) to catch a wider variety of potential credential leaks.
- New language support: SonarQube's industry-leading SAST and taint analysis capabilities now extend to Go and Kotlin, enabling secure development practices for teams using these popular modern languages.
- New security reports: SonarQube now provides reports aligned with the latest CWE Top 25 2024 and OWASP Top 10 Mobile standards. This empowers developers and managers to assess security risks against current industry benchmarks.
These improvements, alongside Advanced Security, make the latest SonarQube release a compelling upgrade for any organization.
The SonarQube advantage: security that works with you
SonarQube Advanced Security delivers a fundamentally better approach to code security - one that empowers developers and streamlines collaboration between development and security teams. Here’s why it stands out:
- Integrated code quality and code security: One integrated platform provides code quality and code security analysis (SAST, advanced SAST, SCA, taint analysis, secrets detection, IaC scanning, security reports) for all popular languages and frameworks, covering first-party, AI-generated, and open source code. No more juggling multiple, disconnected tools.
- Unmatched accuracy & speed: SonarQube is renowned for its high true-positive rate and low false-positive noise, thanks to sophisticated analysis engines like taint analysis and advanced SAST that cover the entire code base. Analysis is fast, designed to integrate smoothly into CI/CD pipelines without causing bottlenecks.
- Seamless workflow integration ("Start Left"): Security is embedded directly into the developer workflow. Get immediate feedback in the IDE via SonarQube IDE extension in connected mode, automated checks in pull requests with clear decorations, and quality gates in your CI/CD pipeline to prevent insecure code from reaching production. This "start left" approach catches issues early when they are easiest and cheapest to fix.
- Actionable remediation: SonarQube doesn't just find problems; it provides clear explanations, highlights the problematic code, and offers guidance with AI CodeFix to help developers understand the issue and fix it quickly and correctly.
- Compliance: Easily track and report on compliance with major security standards like OWASP Top 10, PCI DSS, CWE Top 25, OWASP ASVS, STIG, and CASA. SonarQube also aligns with frameworks like the NIST Secure Software Development Framework (SSDF), simplifying regulatory adherence.
By addressing the common pain points of traditional security tools – noise, friction, and lack of integration – SonarQube Advanced Security fosters developer adoption and enables organizations to ship secure, high-quality software faster.
Availability:
- SonarQube Advanced Security is available as a license for SonarQube Server Enterprise or Data Center Edition 2025.3 and later.
- Support for SonarQube Cloud Enterprise is available as of September 15, 2025.
- Learn more: Visit the(https://www.sonarsource.com/solutions/security/).
- Explore documentation: Server | Cloud
- Try SonarQube Advanced Security: https://www.sonarsource.com/products/sonarqube/advanced-security/free-trial/
- Talk to us: https://www.sonarsource.com/solutions/security/advanced-security-request/